The Evolving Threat of Domain Exploitation and How to Stay Protected

An accounting clerk receives an email from the CEO of his company. Although it seems a bit unusual, he follows the instructions to purchase several gift cards and replies with the gift card ID numbers. The next day, when he asks the CEO about reimbursement, the CEO responds, “What gift cards?”
Had the clerk scrutinized the email address more closely, he would have noticed a slight discrepancy. The message appeared to come from an internal email but was actually a cleverly disguised look-alike. This deception succeeded because the clerk overlooked the minor difference in the email domain address, failing to question the email’s legitimacy. He fell for this phishing scam hook, line, and sinker.
Watch Out for Imposter Domains
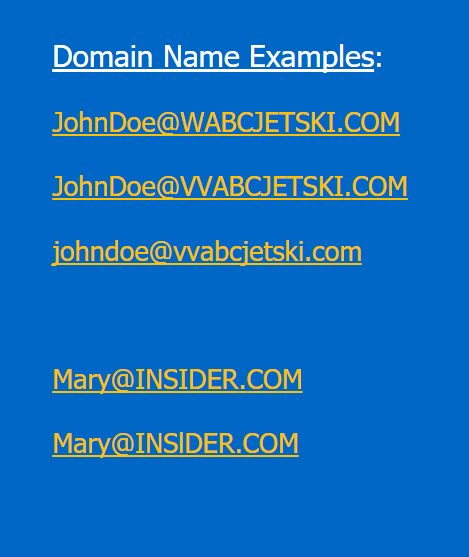
Phishing schemes often employ look-alike domains to exploit victims’ perceptions and trust. Cybercriminals register domain names that closely resemble your legitimate domain by omitting letters, transposing them, or substituting characters with similar-looking ones. For instance, using “rn” to represent “m” or replacing a lowercase “l” with the number “1”. These deceptive tactics can involve characters from various languages, making detection even more challenging.
Exploitation of New Domain Extensions is an Emerging Threat

Cyber-criminals are continually adapting their strategies, now leveraging new generic top-level domains (gTLDs) to enhance phishing attacks. Unlike traditional domains such as ‘.com’ or ‘.org’, these new gTLDs include extensions like ‘.shop’, ‘.xyz’, and ‘.zip’.
A study by Interisle Consulting revealed that while new gTLDs account for only 11% of new domain registrations, they were linked to approximately 37% of reported cybercrime domains between September 2023 and August 2024. This disproportionate representation points out the appeal of these domains to cybercriminals.
For example, the ‘.zip’ domain, introduced by Google, mirrors the ‘.zip’ file extension. This similarity has been exploited in phishing attacks, as users might mistake a ‘.zip’ URL for a legitimate compressed file link.
Purchase Your Own Domain Look-Alikes
To thwart hackers attempting to mimic your internal email addresses, it’s essential to control your domain neighborhood by acquiring potential look-alike domains. By purchasing these domains yourself, you prevent malicious actors from exploiting them and ensure they don’t expire under your ownership.
However, with over 1,500 generic top-level domains (gTLDs) available, securing all possible extensions for your domain is neither practical nor cost-effective. Instead, focus on a targeted approach:
Start with Core Domains

Register your primary domain across the most common and trusted extensions, such as .com, .net, and country-specific options like .co .us or .ca.
Prioritize High-Risk Extensions
Secure gTLDs that could be easily exploited, such as .zip, .shop, or .app, which are commonly used in phishing schemes.
Defensive Purchases
Consider look-alike variations that mimic your domain through typosquatting (e.g., replacing an “l” with a “1”) or misspellings. For example, at XPERTECHS, we might purchase xpertek.com, expertechs.com, and xprtechs.com.
Monitor for New Threats
Use domain monitoring tools to stay vigilant about emerging threats, identifying unauthorized registrations that could harm your business.
While securing your domain neighborhood is an important step, it’s only one part of your cyber defense strategy. To truly protect against cyber threats, you need a multi-layered cybersecurity strategy that guards every aspect of your business.
Best Cybersecurity Approach is Layered
Defending your data and business from hacker tactics like phishing and domain impersonation requires multiple layers of defense. Here’s how a layered strategy can protect your organization:

Utilize Advanced Technical Security
Implement antivirus, antimalware, and spam filters. Keep software patched and up-to-date and ensure your IT team monitors for intrusions while leveraging built-in security features like Microsoft 365 Business tools.
Establish and Maintain Security Policies
Remember, a substantial portion of your cybersecurity plan is non-technical. Employees should be trained to handle data and network access in ways that minimize risk while following company policies for secure behavior.
Cybersecurity Awareness Training
Providing employees with ongoing cybersecurity training is one of the most effective ways to protect your business. Training should include:
- Scrutinizing URLs to spot unusual extensions like .zip or .xyz.
- Recognizing look-alike domains and typosquatting techniques.
- Verifying suspicious messages with known contacts.
- Staying alert for red flags like unexpected urgency in messages.
Related: How to Get People to Care About Cybersecurity
Need More Cybersecurity Peace of Mind?
If you’re not confident that your IT team has all the bases covered when it comes to cybersecurity, give us a call to schedule a security consultation.
