CMMC Compliance: Choosing Your Path Forward

You know you need CMMC compliance. Maybe it showed up in a contract requirement, or you’re preparing for future government contracting opportunities. Either way, you’re dealing with compliance requirements that involve unfamiliar terminology and documentation beyond normal IT work.
Other companies who work with government agencies, including the Department of Defense, are in the same position as Cybersecurity Maturity Model Certification (CMMC) has moved from planning to enforcement, and the questions are piling up. What level do you need? What systems should be included? Should you handle this internally or bring in outside help? How do you know who to trust?
This guide takes you from understanding what CMMC requires through the decision points that determine your path forward. Whether you’re just starting to learn about the framework or you’re deep in the compliance process and reconsidering your approach, you’ll find what you need to make informed decisions.
In this guide:
What CMMC Is and Who Needs It
CMMC was created to establish consistent cybersecurity standards throughout the government contractor network. Every organization working on DoD or other types of government contracts—whether you’re handling basic administrative data or classified material—falls under these requirements.
The framework started in 2020 with five levels and complex requirements that overwhelmed small businesses. CMMC 2.0 was released in 2021, cutting it down to three levels and simplifying the requirements to align more closely with standards from the National Institute of Standards and Technology (NIST)—guidelines many companies already knew. They also added self-assessment options for lower levels and gave companies a path to certification even while closing security gaps.
The Final Rule came out in late 2024, making CMMC 2.0 official. Requirements are now showing up in contracts. Enforcement is rolling out gradually, but it’s happening.
CMMC Applies to Government Contractors
You need to comply with CMMC if you’re part of the DoD contractor network or if you work with one of the many other government agencies that are requiring CMMC compliance. Prime contractors, subcontractors, and specialty providers in construction, engineering, manufacturing, or professional services all fall under these requirements. Size doesn’t exempt you, and neither does being several tiers down the supply chain.
Your specific requirements depend on what kind of data you touch and what your contract says. A company doing basic administrative work faces different standards than one handling sensitive technical specifications. But everyone has requirements to meet.
The Three Levels of CMMC
CMMC 2.0 has three levels, each tied to the type of information you handle and the corresponding security expectations.
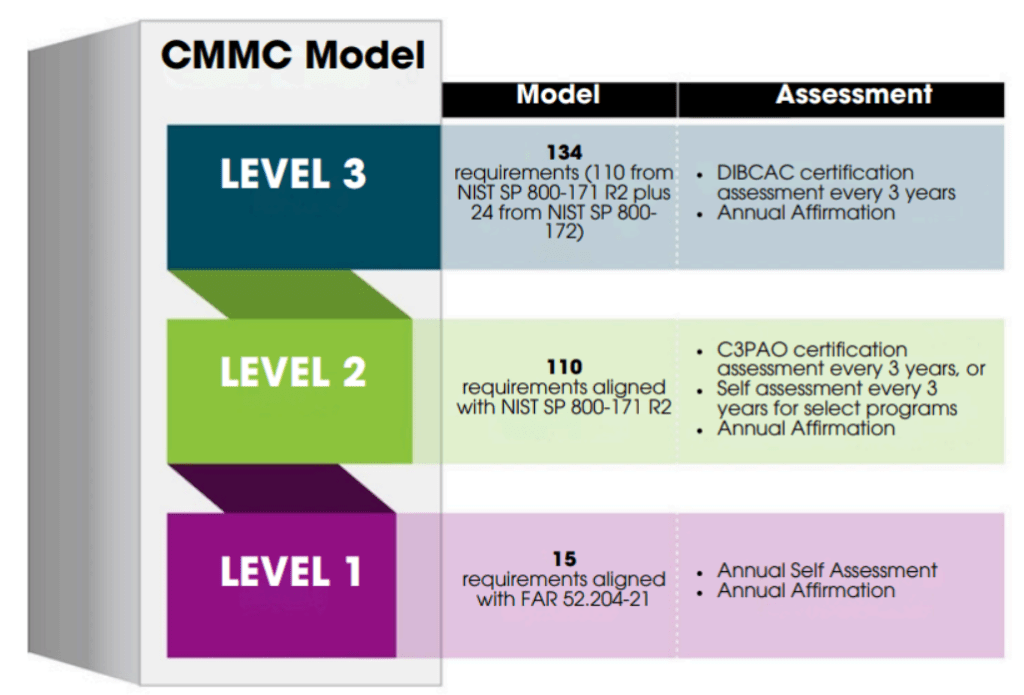
Level 1: 17 Basic Security Practices
Level 1 covers Federal Contract Information (FCI)—the basic unclassified data that comes with government work. You’ll need to demonstrate 17 fundamental practices like updating software regularly, controlling who can access what, and enforcing decent passwords. You handle this through annual self-assessment, with a senior executive signing off that everything’s in place.
Level 2: 110 Controls for Sensitive Information
Level 2 kicks in when you’re dealing with Controlled Unclassified Information (CUI)—data that’s sensitive enough to need serious protection. You’re looking at 110 security controls based on NIST standards. This means encryption, multi-factor authentication, employee training, and considerably more documentation. Depending on your contract, you might self-assess or you might need a third-party assessor to verify everything.
Level 3: Advanced Security for Critical Defense Projects
Level 3 is for contractors on the most critical national security work. The requirements include sophisticated capabilities like continuous monitoring and advanced threat detection. Government assessors run these evaluations. Most small and midsize contractors won’t hit this level.
Your Contract Specifies Your Level
Check your contract or solicitation documents. They’ll specify which level you need. Federal Contract Information (FCI) work typically means Level 1. Controlled Unclassified Information (CUI) work typically means Level 2. But contract language isn’t always crystal clear, especially early in the bidding process.
Your business development or contracts team needs to coordinate with IT early. Together, they should figure out exactly what data types you’ll be handling and what certification level that triggers. Two companies at the same level can face very different work depending on their IT setup and how they handle contract data.
Related: Overview of CMMC and What It Requires
CMMC Compliance Involves Work Beyond IT’s Normal Role

Level 1 might sound basic, but it takes more work than most companies expect. Demands increase as you move up each level with requirements for more documentation and more ongoing attention.
CMMC requires work your IT team doesn’t typically handle. Beyond implementing security controls, you’ll need to map how data flows across your organization, write formal policies that span IT, HR, and operations, create documentation that proves controls are working, and prepare everything for outside review. Then you have to maintain it all and renew annually.
Companies think they’re already compliant because they have security tools in place. Then they try to document it and realize the gap between having controls and proving you have them according to CMMC’s framework.
Where Companies Get Stuck
1. Not Knowing Where to Start
You’ve got a contract that references CMMC but translating that into concrete next steps isn’t obvious. Which department owns this? What do you tackle before everything else? Who even needs to be in the room?
The worst part is managing this alongside regular work. Compliance starts feeling like a second job no one was trained for. You’re running a business, not training cybersecurity specialists, but now your team needs enough expertise to get through assessment.
2. Overscoping Your IT Environment
A lot of companies assume every system, every user, every process needs to meet CMMC standards. Sometimes that’s true, but often it’s not. If a system never touches Federal Contract Information or Controlled Unclassified Information, you might be able to exclude it entirely.
The problem is proving exclusion takes just as much work as inclusion if you don’t know how. And once you’ve drawn your boundaries too wide, pulling them back means reworking everything. Getting scoping right from the start means understanding your data flows—where information comes in, where it’s stored, who can get to it, and where it goes.
3. Missing or Incomplete Documentation
Having security controls isn’t enough. You need documentation proving those controls exist, showing how they work, and demonstrating they’re maintained consistently. A lot of companies have invested in good security tools but haven’t kept up with the paperwork side.
Security practices also tend to evolve faster than documentation. Someone implements a new control, it works, everyone moves on. Then six months later you’re scrambling to document what you did and why. A Registered Practitioner knows what assessors need to see and can help structure documentation to match both your operations and CMMC’s requirements.
4. Keeping Up With Changes
Getting compliant once doesn’t mean you’re done. The Final Rule established the framework, but details keep evolving. For example, in the future, standards will move to the latest NIST version. Staying compliant means regular documentation reviews, periodic reassessments, and tracking regulatory updates, so you know when requirements shift.
Related: Overcoming the Top CMMC Compliance Challenges
Should You Handle This In-House or Bring In a Partner?
Every company eventually hits this question. The answer depends on your team’s CMMC knowledge, the time you can commit, and your confidence in building documentation that will hold up under scrutiny.

Questions to Ask Before Deciding
If you’re considering an internal approach:
- Does anyone on your team have direct experience with CMMC or similar frameworks?
- Would having a Registered Practitioner or Registered Practitioner Organization guide the process make sense?
- Can your team realistically handle the documentation workload, or would templates and expert guidance make it manageable?
- How comfortable are you interpreting contract requirements and translating them into security practices?
- When your CEO signs that affirmation, will you feel confident about what’s being submitted?
Uncertainty on any of these questions suggests you’d benefit from outside help.
How the Two Approaches Compare
| Factor | Internal Team | Partner Support |
|---|---|---|
| Time Investment | Your team spends significant time learning CMMC and figuring out how to apply it | Your team still invests time, but less of it is spent figuring things out |
| Required Knowledge | Someone needs to master CMMC framework, NIST standards, and contract interpretation | Registered Practitioners bring framework expertise and assessment experience |
| Error Risk | Higher chance of scope mistakes, incomplete evidence, incorrect assumptions | Early guidance prevents common mistakes, identifies gaps before they become problems |
| True Cost | Looks cheaper initially but internal hours add up, mistakes cost time and opportunities | Known cost up front, less strain on your team, faster path to certification |
| Long-Term Maintenance | Knowledge walks out the door with staff changes, documentation gets lost or outdated | Continuous documentation updates, regulatory tracking, repeatable annual process |
Related: CMMC Compliance: Should You Handle It In-House or Work with an MSP?
What to Look for in a CMMC Partner
Once you’ve decided outside help makes sense, you need to separate providers who have invested in CMMC expertise from those treating it as just another service line.

1. Questions before solutions.
Before describing their process, they should want to understand your contracts, your current security setup, and where your data lives. A provider jumping straight to their pitch hasn’t done enough discovery.
2. Scoping gets early attention.
Many companies waste resources by treating every system as if it needs CMMC controls. Experienced providers discuss boundaries and exclusions early to keep your effort focused on what matters.
3. They explain their process.
Request a walkthrough of their compliance management system. You want centralized documentation, clear progress indicators, and team collaboration features—not scattered spreadsheets and email chains.
4. Timeline estimates sound realistic.
Providers promising fast turnarounds don’t understand the work involved. Even basic certification requires policy development, evidence gathering, and proper documentation. Honest timelines account for your team’s participation too.
Critical Information Before You Commit
Beyond recognizing expertise, get specifics about the engagement:
- Initial phase clarity. What happens in month one? You should understand onboarding steps, scoping methodology, and initial deliverables before signing anything.
- Your team’s role. Compliance requires participation. Know exactly which stakeholders get involved, what information they’ll provide, and how much time to allocate.
- What you receive. Final deliverables should include organized documentation, completed assessments, and submission-ready files.
- Ongoing relationship. Annual compliance isn’t a repeat of year one. Understand how documentation gets updated, how regulatory changes get tracked, and what continued support includes.
Related: How to Choose the Right CMMC Compliance Partner
How XPERTECHS Approaches CMMC Compliance
XPERTECHS is a CMMC Registered Practitioner Organization. We guide government contractors and suppliers through the compliance process with a structured approach: assess your current cybersecurity posture against CMMC standards, create a compliance plan that addresses gaps, provide implementation guidance, and deliver continuous support as regulations evolve.
Our certified experts handle the CMMC complexities so your internal team can focus on business objectives. You gain access to specialized expertise without building an in-house compliance team. We provide a customized roadmap that accelerates your path to compliance, with ongoing oversight to keep you aligned with evolving standards.
Your Next Steps
If your team has the expertise and capacity to manage compliance internally, go for it. But if you’re facing tight deadlines, unclear requirements, or stretched resources, bringing in someone with direct CMMC experience makes sense.
CMMC requirements are already appearing in government contracts. Starting early gives you options. Waiting leaves you reacting.
Ready to explore what CMMC support might look like for your business? Get in touch and we’ll walk you through it.
