Top Telltale Signs of Phishing

You wouldn’t think that people would fall for the same old trick again and again, but they do. That’s why phishing remains a prime tactic for cyber criminals who would rather get someone to open the door for them instead of trying to bust through technical barriers to get to your IT systems and company accounts. Billions of spam emails flood the internet trying to get into inboxes everywhere. Spam filters catch a lot of them but too many still get through and people are clicking on them.
The Anti-Phishing Working Group (APWG) reports that Q2 2022 set a record for having the most observed phishing attacks. Business email compromise (BEC) remains a favorite phishing technique for bad guys to attack both large and small businesses. Whether the phishing email is impersonating your company’s CEO or trying to get your Microsoft login credentials, training is critical to equip your people to recognize these scams.
Phishing – Attempts to get a person to click on a link or open an attachment in order to download malware, or open to a web page where account login credentials are requested. Phishing is delivered primarily through email, text messages and web pages.
When it comes to training people to recognize a phishing email when they see one, one workshop a year doesn’t cut it. Ongoing training is necessary to keep secure behavior in the forefront of employees’ minds and to stay up to date with the latest trends in phishing.
There are many different training providers, such as KnowBe4, and the cost is very reasonable especially when you consider that phishing, business email compromise and stolen company credentials are three of the top four cyber criminal preferences.
It’s easy to get started with cybersecurity awareness training, but you might not be doing it today so, we’re going to help you get started by teaching you some signs that a phishing email made it to your inbox.
How to Spot a Potential Phishing Email
1. ALL CAPITAL LETTERS
Many times, a phishing attempt will try to get your attention by using all capital letters, especially in the subject line. This is to make you think that the email is of high importance when in fact, it’s an attempt to get you to click a link or download an attachment to your machine.
If you open one of these messages, exit out immediately without clicking any links or attachments and inform your IT team.
2. Blank “To:” and “CC:” Fields
Another easy give away that the email you received is a phishing scam is if the “To:” and “CC:” fields are blank. They’re blank because the cyber criminal used the “BCC:” field which hides individual addresses. This means the message was not sent just to you, but to a whole list of possible victims. Success for hackers is a numbers game so they send the message out to as many targets as possible.
If you notice an email with a blank “To:” field, delete it immediately. Do not click any links or open any files that are attached to the message.

3. Questionable Link Destinations
A popular way for hackers to get the information and/or access they want is to include a link for a unaware user to click. These links either download some sort of malware onto your machine, or send you to a page where they ask for you to provide personal information, such as your social security number or bank account info.
An example would be if you received an email from Verizon to pay a bill but the link to click takes you to a domain that does not appear to be for Verizon. If you see an email like this, exit immediately and follow-up with your network administrator to validate its authenticity.
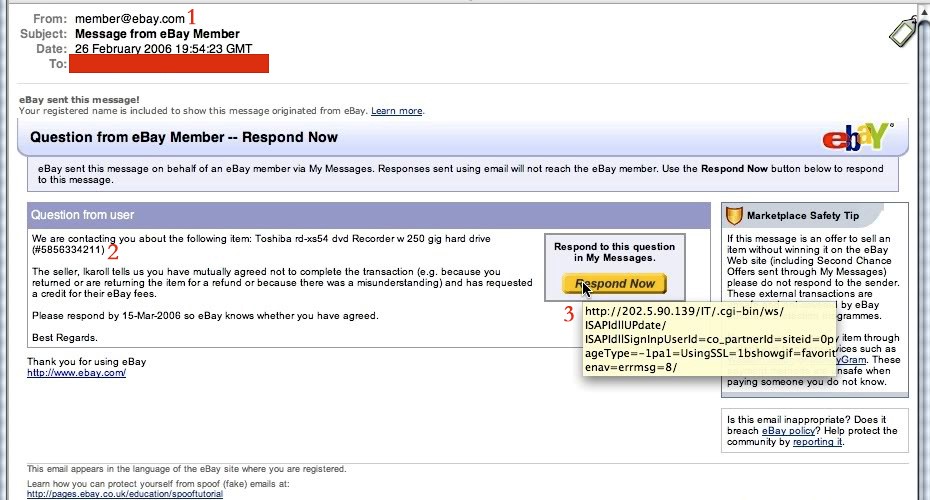
A good way to tell if a link is legitimate is to hover over it with your cursor and see where the link takes you. If the website looks unfamiliar or does not match where the email says it should be going, then DO NOT click!
4. Look-Alike Domains
Along with questionable link destinations is the practice of mimicking your domain name with one that looks like it. To accomplish this, hackers put together characters to resemble something else. For example they might put and “r” and ‘n” together “rn” to look like an “m”.
This ploy is used to impersonate people in your company like the CEO. When an employee gets a message from an authority figure like that, they’re likely to do whatever is requested of them – like buy some gift cards or change the banking information for a vendor.
Look closely at email addresses, not just the display name to see if the email is from a look-alike domain. You can prevent hackers from using this ploy by buying up domain names that could be confused for your real domain.
Related: Learn about look-alike domains by reading Control Your Domain Neighborhood
5. Requests for Credentials or to Change Financial Arrangements
Perhaps the best sign of a suspicious message is the message itself. What does the sender want the recipient to do? If the request has anything at all to do with finances or login credentials, question it. Instruct employees to send questionable messages to IT if they’re not sure.
In the case of a request for money or to change banking instructions, put verification by a method other than email in your policies and procedures.
Related: How to Stop a Cyber Attack with a Simple Phone Call
Fight Phishing with Tech Tools and Savvy Users
It takes both technical and non-technical security tactics to defend your organization from phishing attacks. Advanced tech tools work to keep fraudulent email out of company inboxes but it’s not fool proof. Employees have to be on their guard.
Up Your Security Game to Managed Cyber Risk
Are you confident in your IT team’s ability to stand up a security posture that will help you effective manage cyber risk? If not, it’s time to up your game with a partner you can trust.
At XPERTECHS, our team of tech experts provide industry-leading managed IT support and cybersecurity services that cater to the needs of your organization with more know-how, more communication, and more commitment. Contact us today for a security consultation and to learn more about how we can shield your organization from phishing and cyber-attacks.
